My Binus' Blog
Just another Binusian blog site
Week 5 – Enumerating
Author: kevintarada19 Jun
This week I learned about enumeration. Enumeration is the process of extracting user names, machine names, network resources, shares and services from a system. The gathered information is used to identify the vulnerabilities or weak points in system security and tries to exploit in the System gaining phase.
Some tools for enumerating such as DumpSec, Hyena, NessusWX, which have GUI and wpscan, TheHarvester, Nmap and nbtScan. But not all of them is available in Kali, so some we must install it ourselves. We are also taught how to install a tool in kali linux step by step, so in the class we installed nbtScan together. NbtScan itself is a tool which can be use to scan a range of ip addresses for enumeration.
Week 4 – Footprinting and Fingerprinting
Author: kevintarada19 Jun
This week i think is the hardest, since fingerprinting and footprinting is very confusing. I learned that footprinting is more to outer layer of information level and fingerprinting is more to the inner layer. The difference is footprinting is about the social information of the server like their relations, while fingerprinting is more to it’s IP or OS running on the system which is a crucial information to take over the server.
One of the tools for fingerprinting is nmap, it tests the response of the remote system to undefined combinations of TCP flags, TCP Initial Sequence Number (ISN) sampling, determining the default setting of the DF bit, TCP initial windows size, ToS setting, fragmentation handling, types and order of TCP options those such as DF, Tos, ISN is an IPID.
Week 3 – Search Engines
Author: kevintarada19 Jun
This week is more exciting, since we start to use the tools in Kali Linux. The tools we used are for searching information on our target, these information such as email, phone number, and sub domains related to our target is very useful for further step of pentesting.
The first tool is theHarvester which is very easy to use. to use theHarvester, we just need to type ‘theharvester’ followed by ‘-d’ followed by our target’s domain, then ‘-b’ followed by the source where theHarvester will try to crawl for informations on our target (may be google, facebook, twitter). There’s also additional functions such as ‘-l’ to specify the limit of results we want to display.
Another tool is whois, it is more to get the information on who owns our target and their social information.
Another useful tool with better GUI than theHarvester is maltego, maltego is more graphical than theHarvester due to it’s GUI, but we need to sign up first to use maltego.
Week 2 – Procedures
Author: kevintarada19 Jun
This week, my lecturer, Sir Kalpin taught the class more on the procedures of Penetration Testing. In order to not break the law or cause any harm to ourselves and the client’s system, we must first:
- Make a written agreement signed by both party
- Confirm that the system we are going to penetration test is our client’s, or at least confirm that our client have the legal rights over the system
After completing the above steps, then we proceed to target scoping which is also very important. We must make an agreement with our client on what’s going to be tested, this step is important in order to avoid breaking the client’s system due to no backup or recovery. Some examples might be, if the system is a running system and we don’t do target scoping agreement first, then we try to do DDos attack, then the server may breakdown and furthermore, if the client don’t have the backup this will cause many losses.
Week 1 – Methodology
Author: kevintarada16 May
In week 1, i learned more about methodology, such as penetration tester who attempt to break into a company’s network to find its weakest link, then reports findings. But then there’s also security tester which is similar with penetration tester, but in addition, they also includes analyzing company’s security policy and procedures. They also offer solutions to secure or protect the network.
I also found new methodology such as crackers, since back then all i know about is only hackers. Where hackers try to access computer system or network without authorization, on the other hand crackers aside from just trying to access computer system or network without authorization, they steal or destroy data too.
I also learned that new inexperienced hackers have their own nickname which is script kiddies, which basically means that they are inexperienced hackers that copy codes and techniques from knowledgeable hackers. This is dangerous since they don’t actually know what the code might do to the target, which is dangerous for them and their target.
Another methodology that is used in a company’s network security team is blue team and red team, they have different roles which red team try to do pentest to the system, it may be without the knowledge of IT staff, and blue team try to defend the system from red team and usually have knowledge of internal system, they may perform a pentest by trying to think about how surprise attacks might occur.
Furthermore i learned that there are 3 model of penetration testing methodology, the White Box model which tester is told everything about the network topology and technology, they are also authorized to interview IT personnel and company employees. Then the Black Box model where company staff does not know about the test and the tester is not given details about the network. This model can be used to test whether the security network are able to detect attacks. Lastly the Gray Box model which tester will be given partial information of the company’s network, so it’s combination of Black and White Box Model.
Construct 2 Project Documentation
Author: kevintarada15 Nov
For my Construct 2 Project, we were told to make a educational game, so we made a chemistry game. In this game you can basically mix up substances to form new substance. So there will be a goal on what you should make, and for every successful substance you make, you get 100 points, but if you submit the wrong substance your life will be deducted by 1 (you have 3 lifes in total).
My team consist of:
- Kevin Tarada
- Longlong Tjandra
- Arnold Widjaja
Here’s a photo of our game:

So what I contributed in this project is on the game logic, I set the logic for the potion/substance mixtures (it’s basically hardcoded with Construct 2 ‘if’ logic), and i also help set the logic so when you put 1 substance in the mixture machine on the left of the screen, it will first check the number of potions variable, if it’s 0 which means the machine isn’t storing any potion at the time, it will store the current substance’s name and when you put another substance, it will first check the machine’s number of potions variable, if it’s 1, then using the hardcoded ‘if’ logic, it will give you the result based on what you put in next and store the result directly to the player’s potion variable not in the machine’s potion variable. Which means the machine will always store 1 potion only at max.
Here’s the logic page:
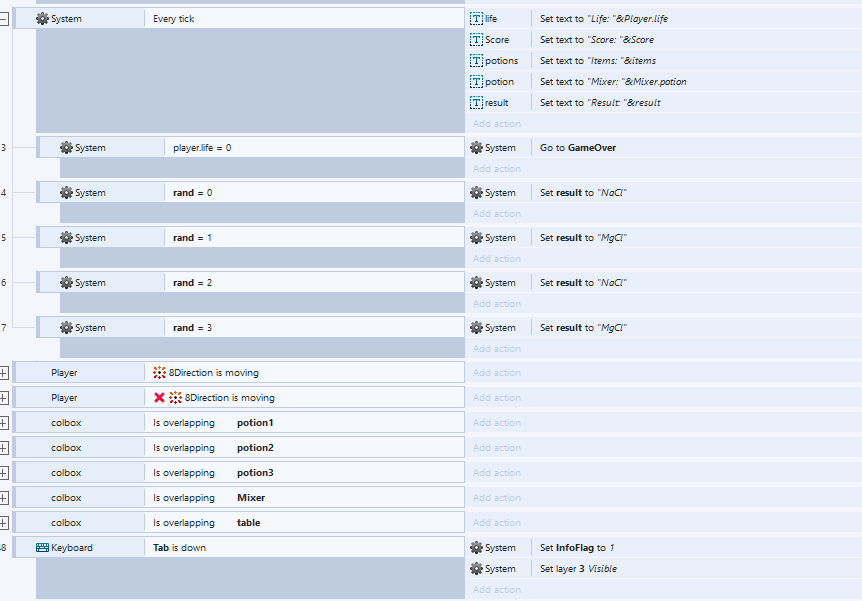
That’s all from my team’s Construct 2 Project. I’ll try to keep update about further project, and thank you for reading this report.
Construct 2 Project Plan
Author: kevintarada4 Oct
For my midterm Final Project, I’m asked to make a game using Construct 2, the game must be an educational game about science, so it’s either about Biology, Physics or Chemistry. For this project we’ll be forming a group of 3, which in my case, my group consist of…
- Kevin Tarada (Me)
- Longlong Tjandra
- Arnold Widjaja
We are planning to make a Chemistry game using Construct 2. So since what we know about Chemistry is that it is related to atoms, in our games you’ll be able to combine several atoms which will fuse up and result to something else. Those combinations will of course be limited but we will try to make various combinations.
That’s all for our Construct 2 Project plan. If we found a better idea to add up to this project, I’ll definitely post it.
Database Final Project
Author: kevintarada28 Apr
So for my second semester Database Management System course final project, my group decided to make a database system for a laptop store.
My group consist of:
- Kevin Tarada (Me)
- Longlong Tjandra
- Arjasa V
Our store later on will have 5 databases:
- Laptops database = contain laptops details
- Laptop’s spare parts database = contain laptops spare parts’ details
- Customer database = store information about the customer (name, address, phone number)
- Transaction database = store the transaction made by the customer, it basically connect the customer database, the item database and employee database
- Employee database = contain the details of the employee
And lastly here’s how we’ve planned to divide our works:
- Laptop database = Kevin T (Me)
- Laptop’s spare parts database = Kevin T (Me)
- Customer database = Longlong T
- Employee database = Arjasa V
- Transaction database = Longlong T
- Visual Studio = Arjasa V
Hello world!
Author: kevintarada26 Mar
Welcome to Binusian blog.
This is the first post of any blog.binusian.org member blog. Edit or delete it, then start blogging!
Happy Blogging 🙂
Recent Comments