My Binus' Blog
Just another Binusian blog site
EHFP – Step 1
Author: kevintarada20 Jun
Step 1
In step 1 we are asked to get user access to the website we’ve been assigned to. I tried is to ping the website assigned, which gives me the ip of the website.
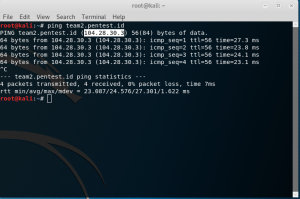
But when i enter the ip to browser, this popped up.
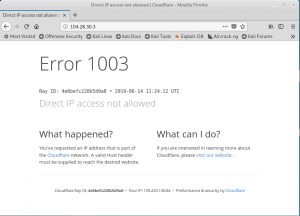
It is written that I’m not allowed to access the website directly through it’s ip, and it is written that the website is a part of cloudflare. Then i tried to google how to find real ip of a website in cloudflare, and censys come out, then i try to input the website to censys website.
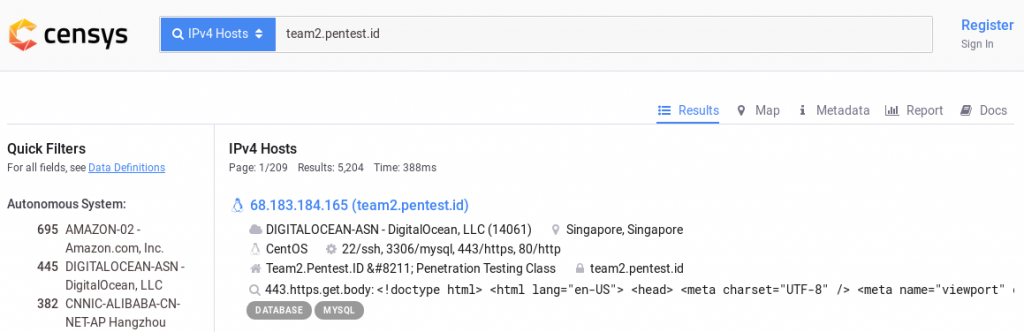
And when i try to input the ip listed in censys, the real website come out, which means it is the ip of the website.
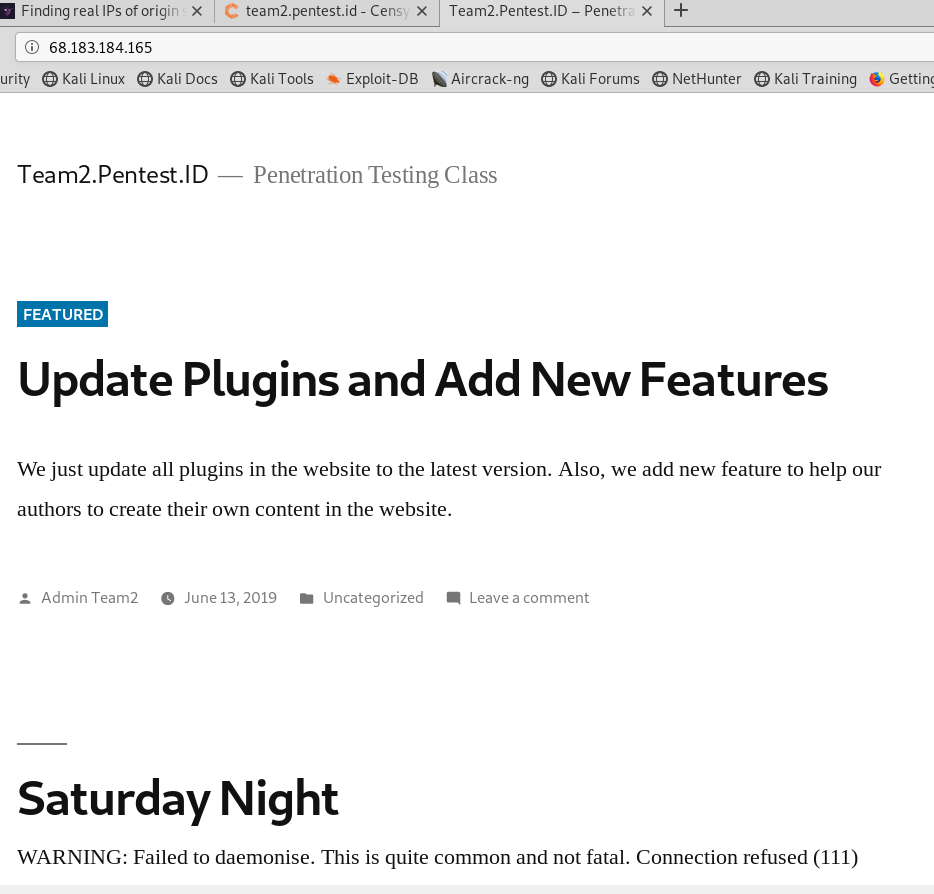
After getting the real ip, I use ‘nikto -h ip -o output -F format’
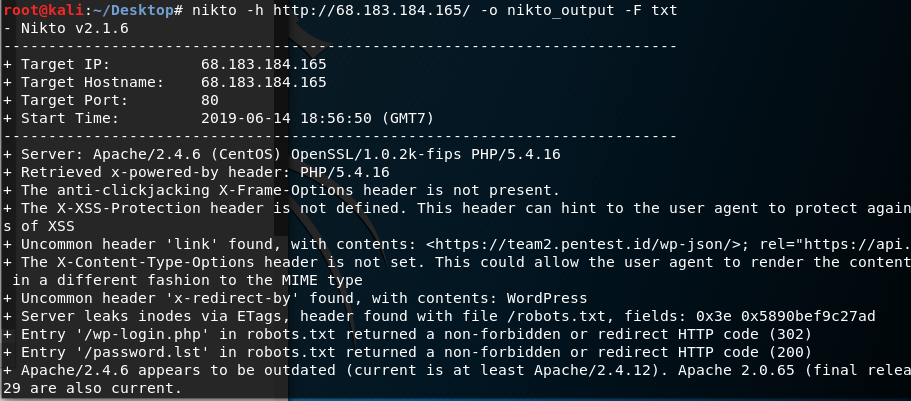
And from the output file this vulnerability is listed,
![]()
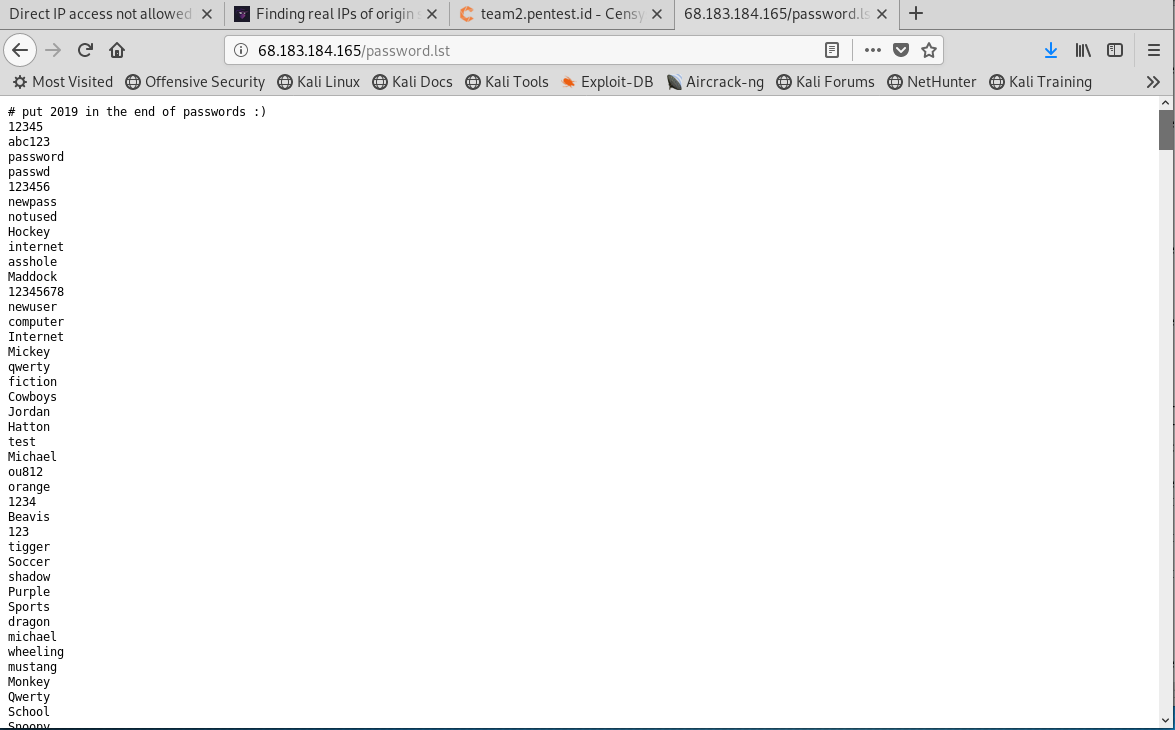
When we download the password.lst the list of possible password is shown, accompanied by a hint on top
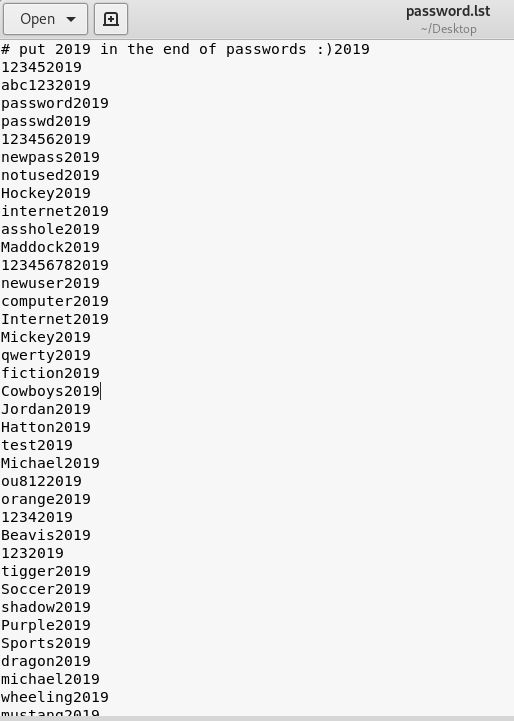
Then i use a kali command to append 2019 to all the passwords
![]()
Resulting in
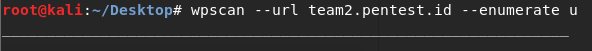
Until here, we’ve got the password list which we will use for bruteforce method. For the username we will use wpscan to enumerate the user and brute force it with the password list.
Result :
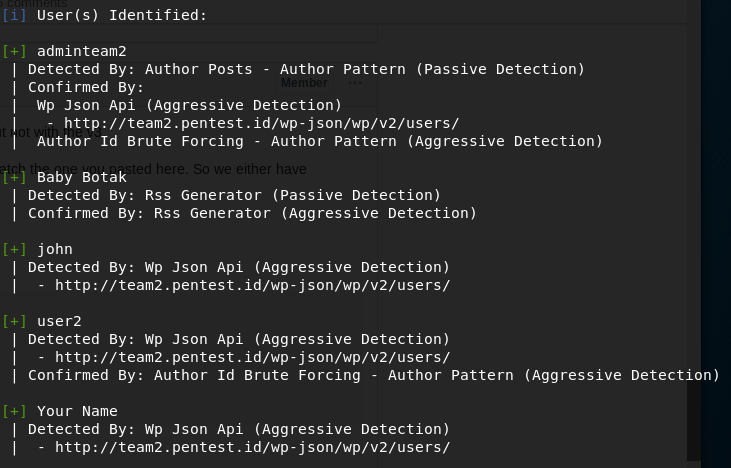
Then from those user we were given a hint that we need to add ‘@’ from one of the users, and since we they are using wordpress to write the blog, in wordpress, if we try to log in with wrong data, their error message shows whether the username is incorrect or the password is incorrect, such as :
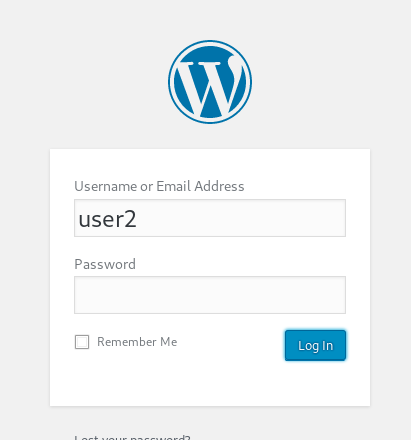
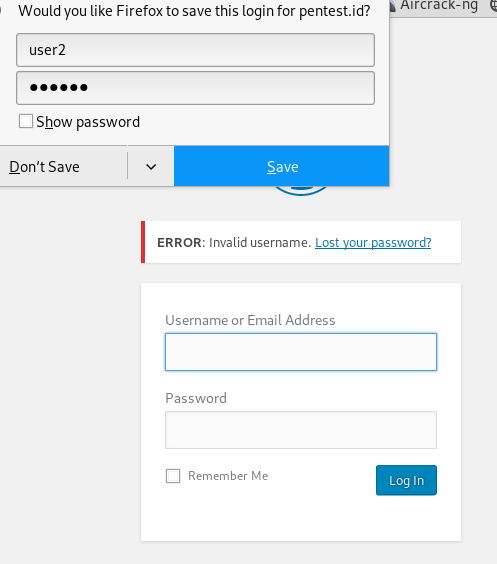
And when we try to add ‘@’ in front of the user, this result come out
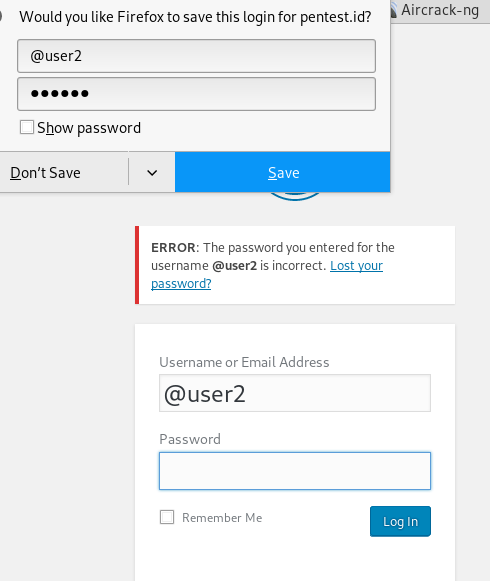
Which means the password is wrong but the username is already correct, showing that it is the valid username.
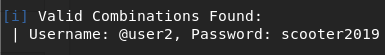
Then by using wpscan using that username and our password list, we try to bruteforce and find the correct pair.
![]()
After several time of processing, we get the user account.
Leave a reply